Recommendation Info About How To Protect Proprietary Information
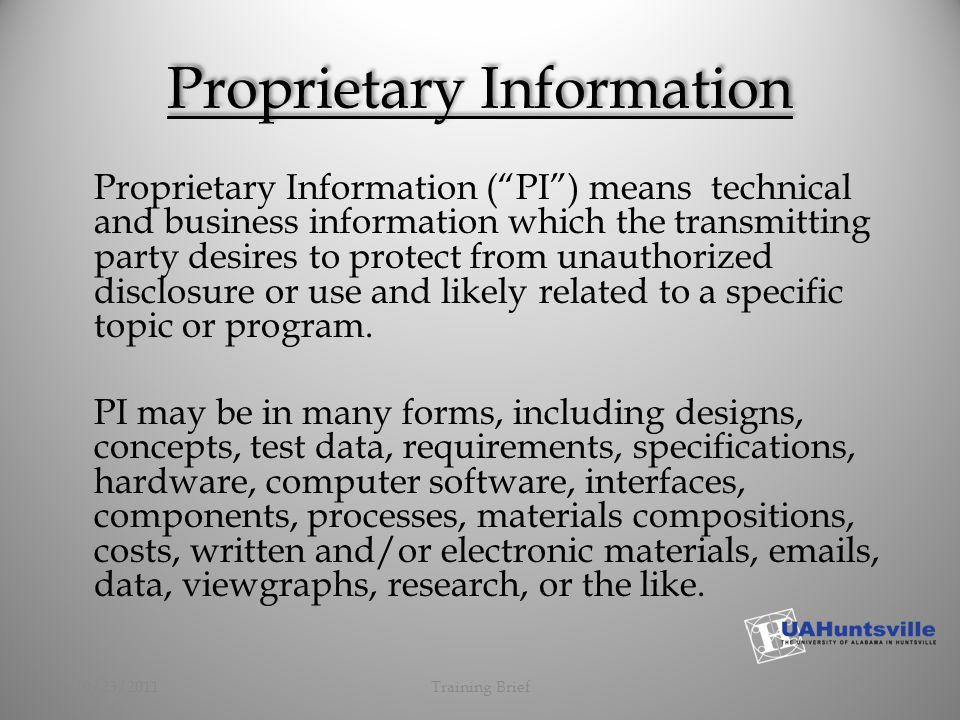
Precisely identifying information that is confidential.
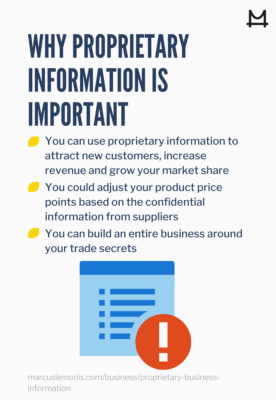
How to protect proprietary information. Also, vet employees to prevent bad. The following matrix provides guidance on how to appropriately handle, protect and mark proprietary information. There are several strategies a company can utilize to help protect its proprietary information.
Nondisclosures before disclosing information to a third party, it is always a best practice to. The very future of your business could be at stake if you don’t control and protect your proprietary data. Staff members should keep proprietary information out of sight or turned over when those who should not see the information are in the office or have access to the office.
Keeping your proprietary information corralled to only those that need to know having a legal agreement in place in. Some of the steps necessary to protect your confidential information include: Information that is privileged, must be marked with one of the following:
Most commonly, the request is for a copy of a contract, but i have seen requests for other proprietary information including complete copies of proposals. Containing trade secrets or commercial or financial. Placement of proprietary markings • when in hardcopy form,.
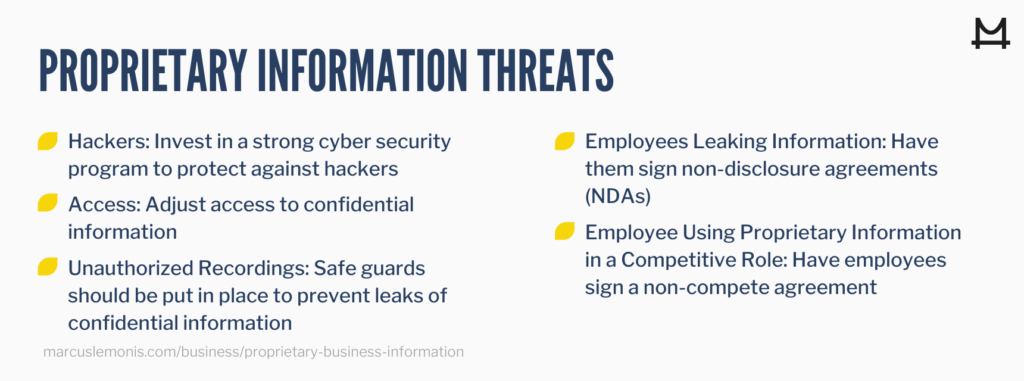
Contain proprietary information, each line or paragraph. Your best bet is to protect yourself upfront by: Analysis of how the increase in remote access has.
Protecting proprietary information in the remote work environment: Contracts are the best tools for protecting proprietary information. Check your control over proprietary data, and regularly audit what critical information you have and who has access to that data.